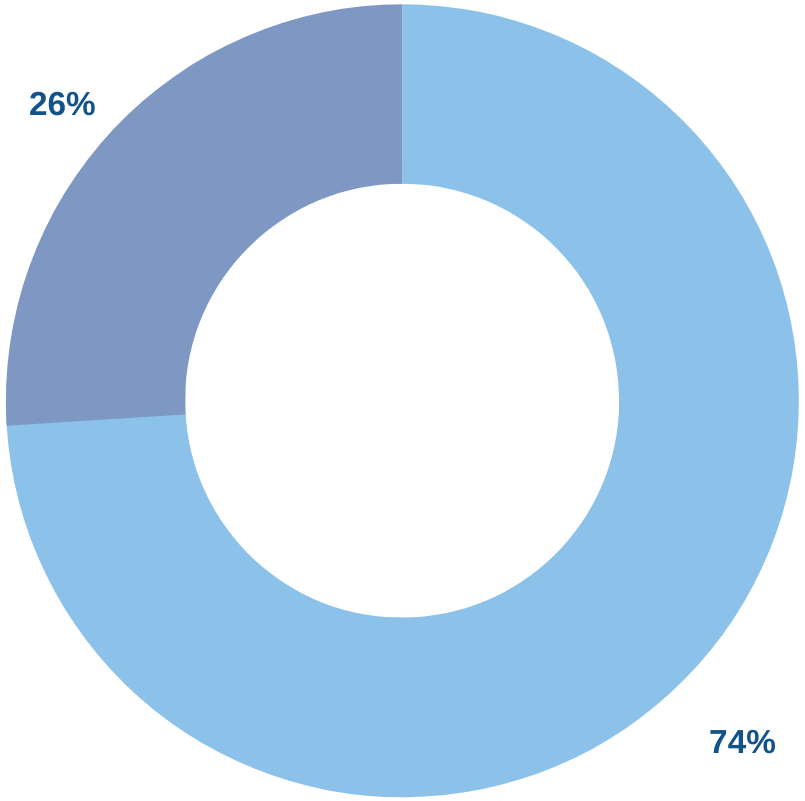
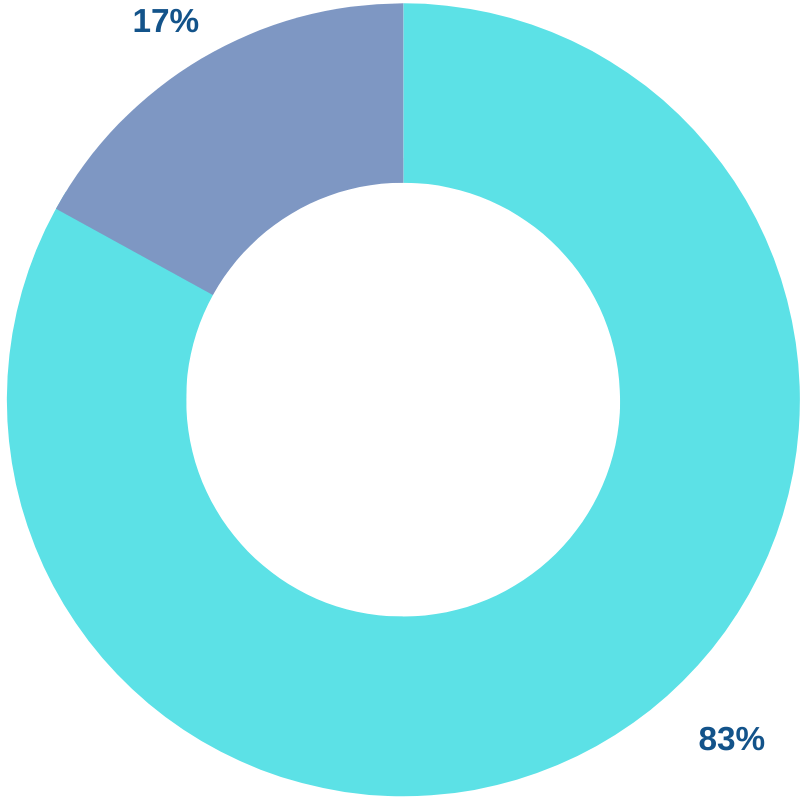
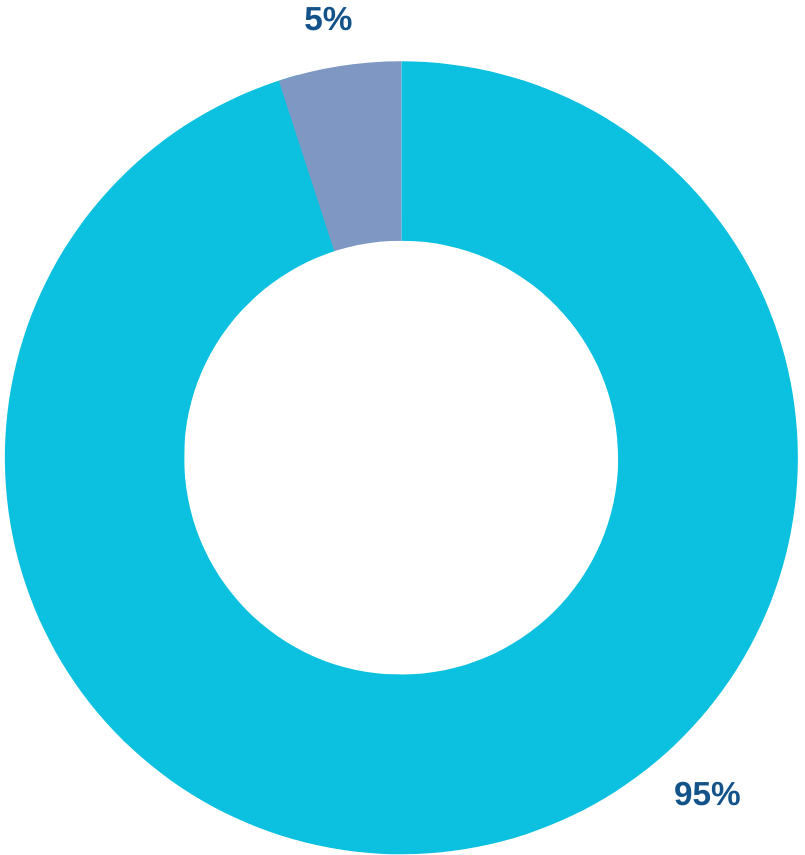
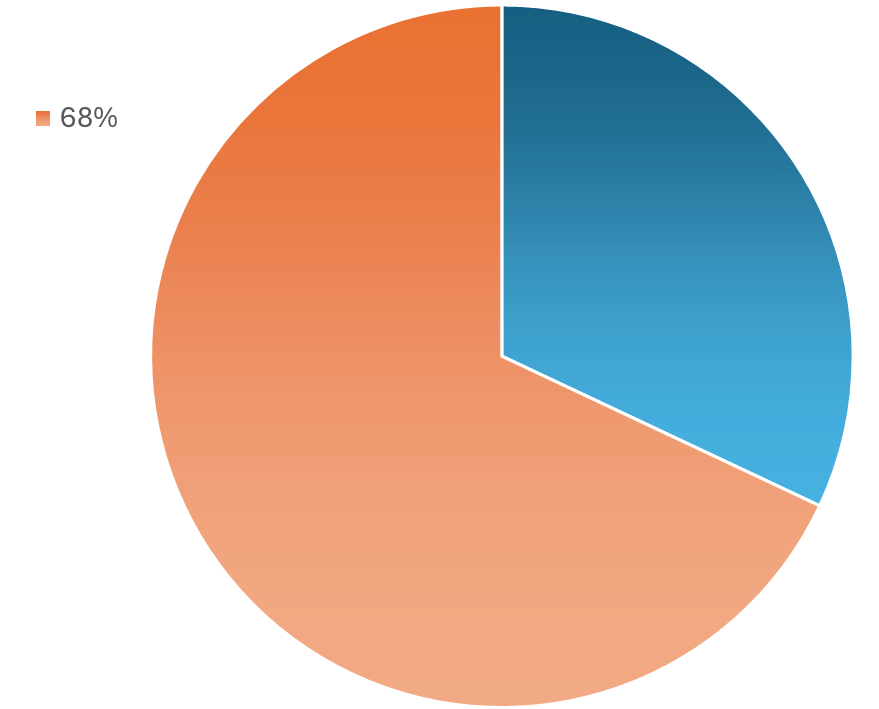
The Human Element
The human element is the most common threat vector, with 68% of cyberattacks involve a non-malicious human element.
— Verizon 2024 Data Breach Investigations Report
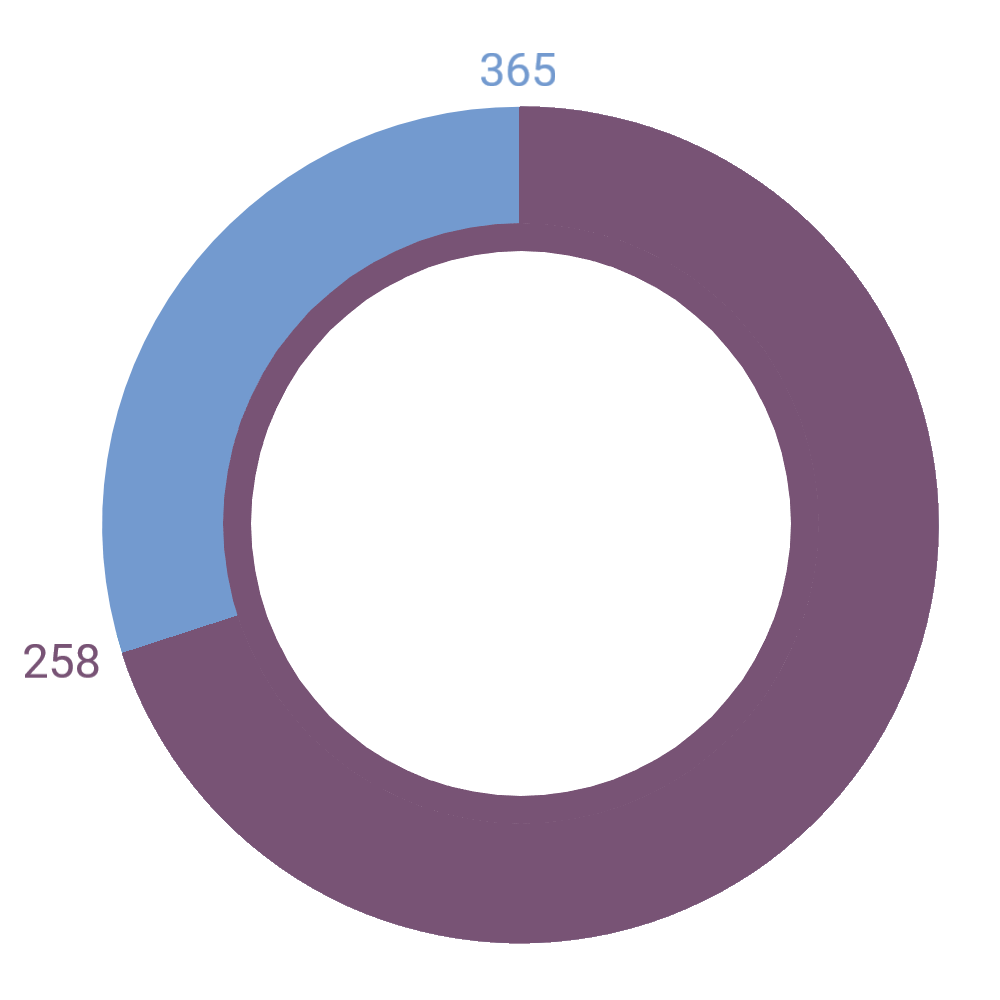
Data Breach Detection
According to “Cost of a Data Breach Report 2024”, it takes an average of 258 days for security teams to identify and contain a data breach.
— IBM and Ponemon Institute
Mobile Attacks
Mobile attacks involving malware, adware or potentially unwanted apps dropped by 13% in Q3, 2024 to a total of 6,686,375. The figure is still above the early 2023 level.
— Malware Report Q3, 2024, Kaspersky Lab
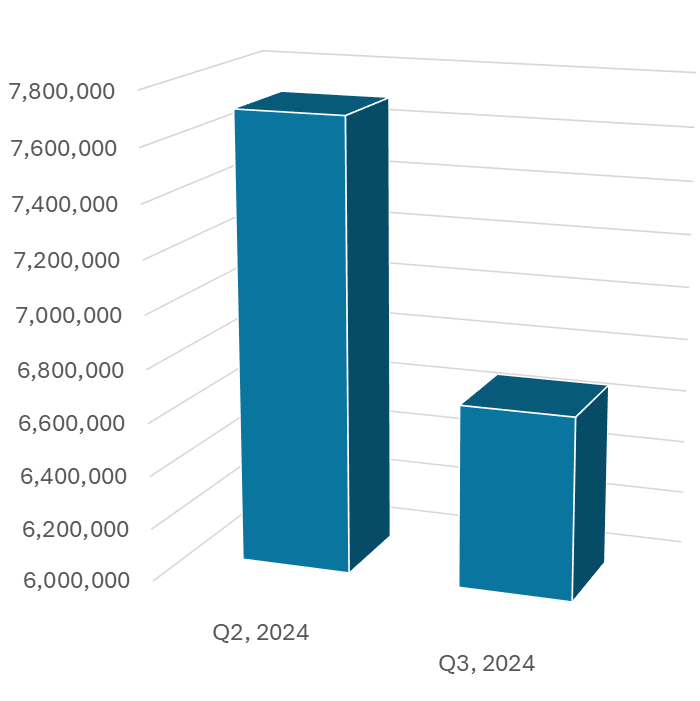
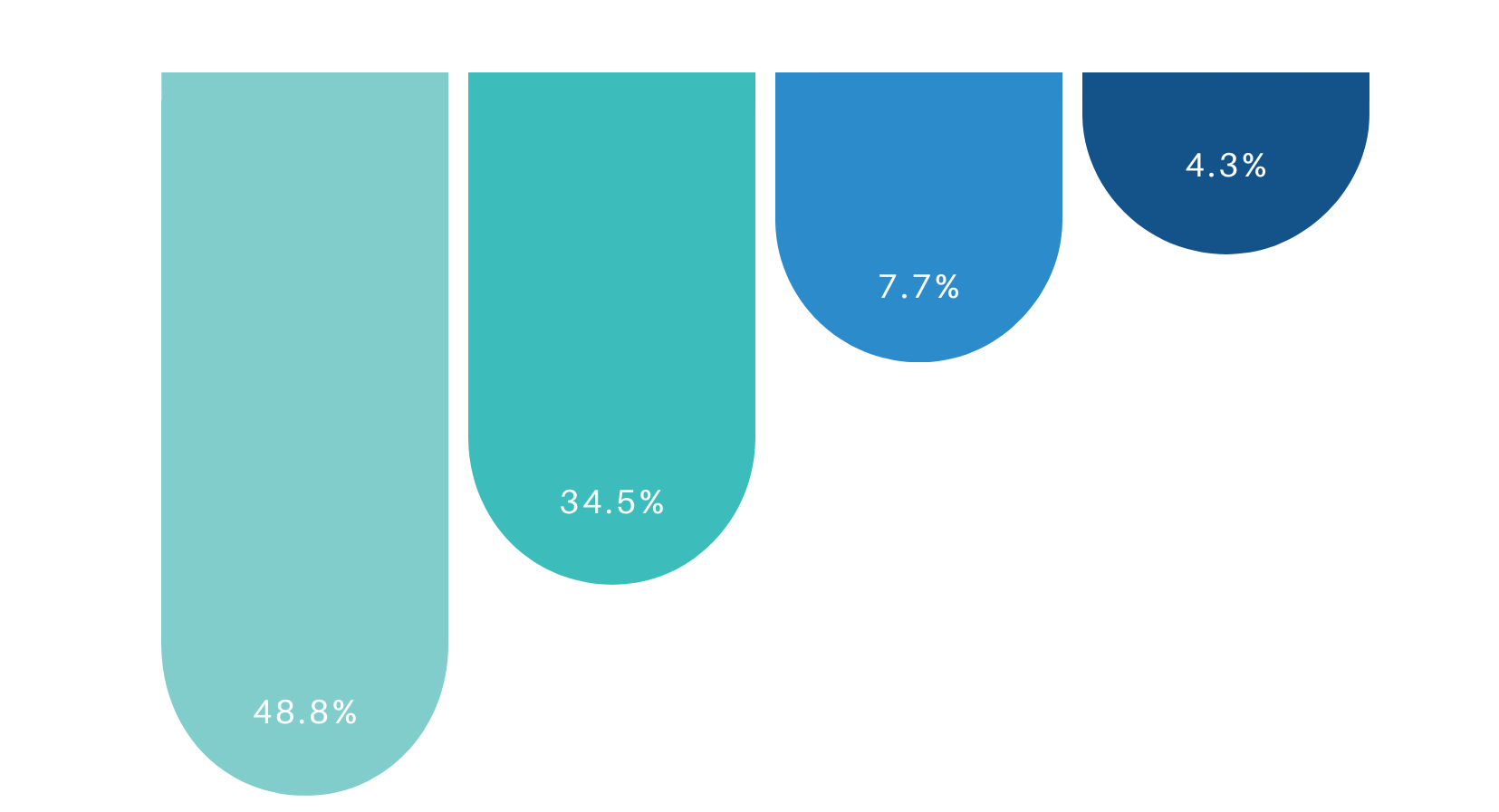
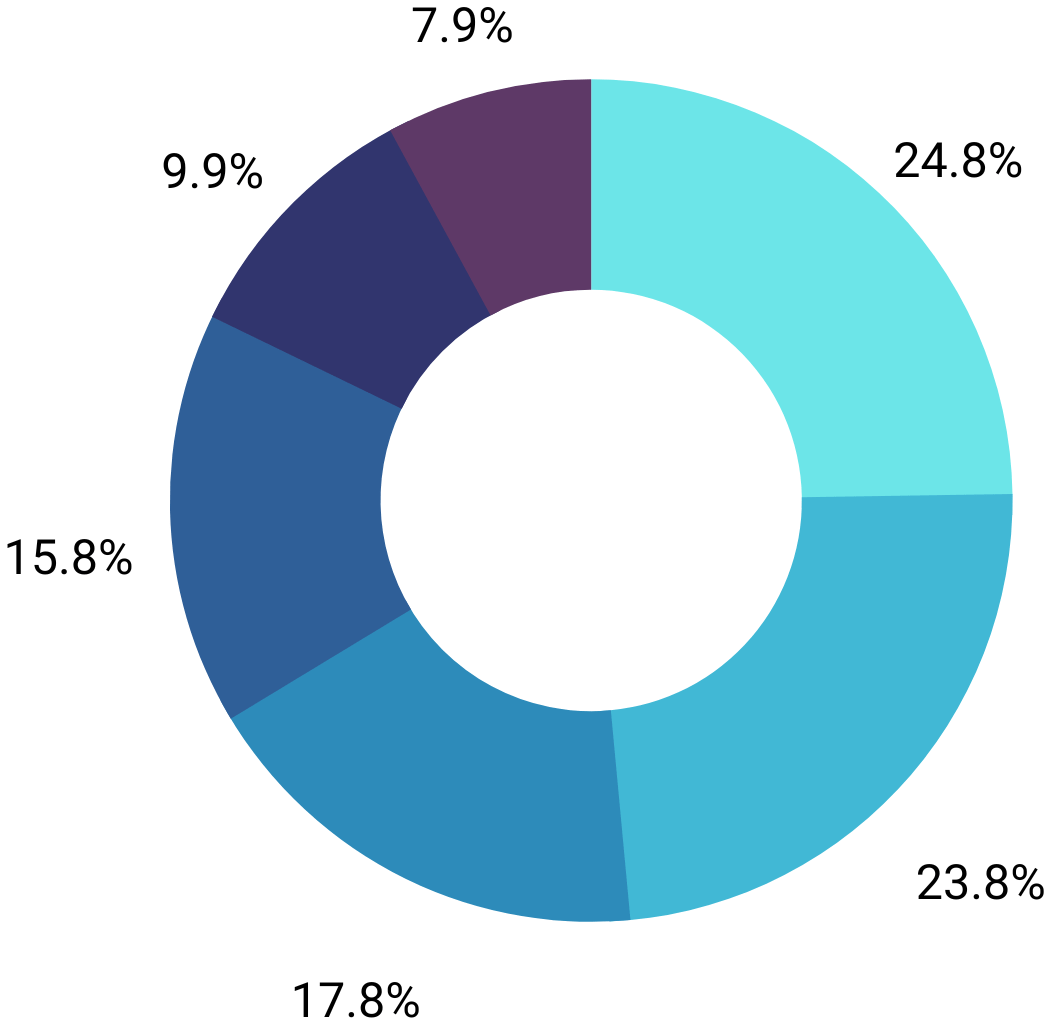
The Executives’ Report
- Executives who experienced more than 1 cyber event.
- Executives who experienced 1 cyber event.
- Executives who reported that their organizations’ accounting and financial data were targeted.
- Executives who expect cyberattacks targeting their organizations’ accounting and financial data to increase in the year ahead.
— Delloite Center For Controllership
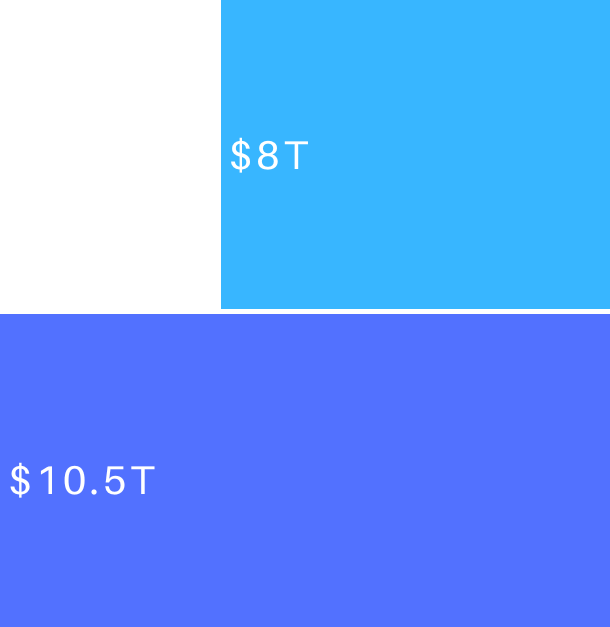
Cost of Cybercrime
According to Cybersecurity Ventures, the cost of cybercrime is predicted to hit $8 trillion in 2023 and will grow to $10.5 trillion by 2025.
Average Ransom Payment in Q4 2022
+58% from Q3 2022
— CoveWare Quarterly Report
External Actors
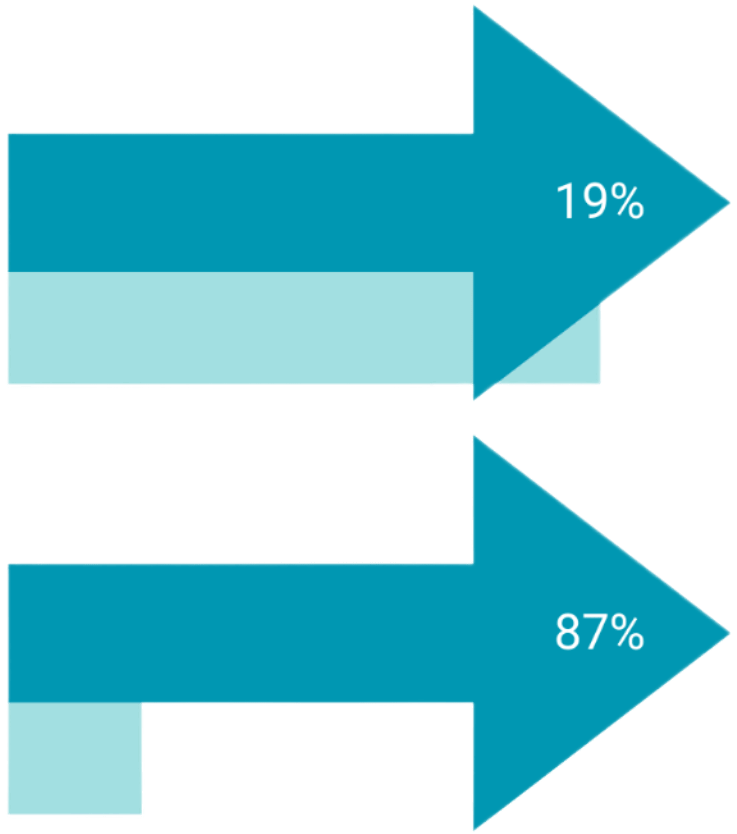
Intrusion Attempts & IoT malware
The number of overall intrusion attempts in 2022 hit 6.3 trillion, a 19% increase from 2021.
IoT malware jumped 87% year over year to a new high of 112.3 million.
— 2023 SonicWall Cyber Threat Report
Data Breach Lifecycle
The average number of days that security teams need to identify and contain a data breach.
— Cost of a Data Breach 2022.
Breaches disclosed by an attacker had a nearly 80 days longer lifecycle compared to those identified internally.
— Cost of a Data Breach 2023, report released by IBM and Ponemon Institute.
VS.
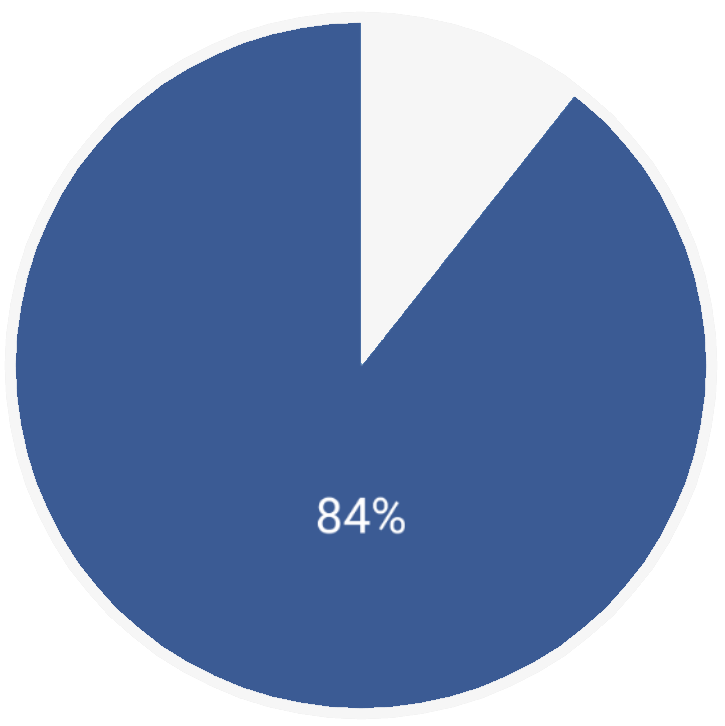
Open Source Software Security
At least one open source vulnerability was found in 84% of code bases.
— Synopsys’ 2023 Open Source Security & Risk Analysis
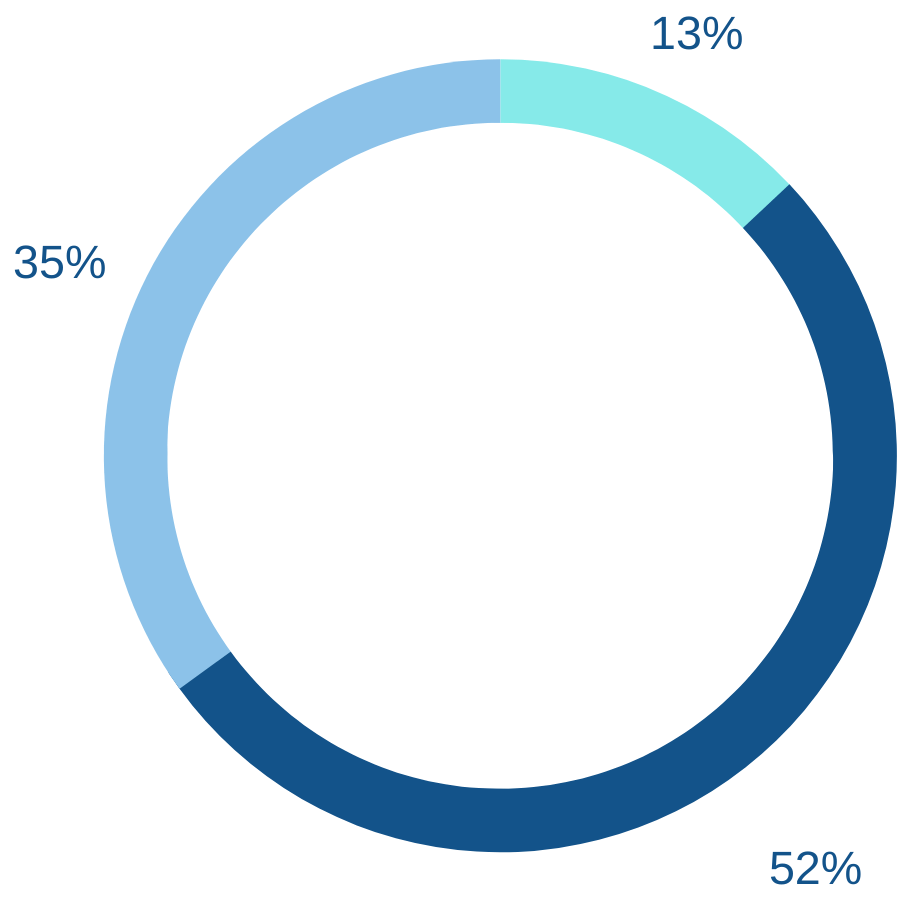
Password Reuse
13% of Americans use the same password across all of their accounts.
52% of Americans use the same password for multiple (but not all) accounts.
35% of Americans don’t reuse passwords.
— 2023 Zippia Research.
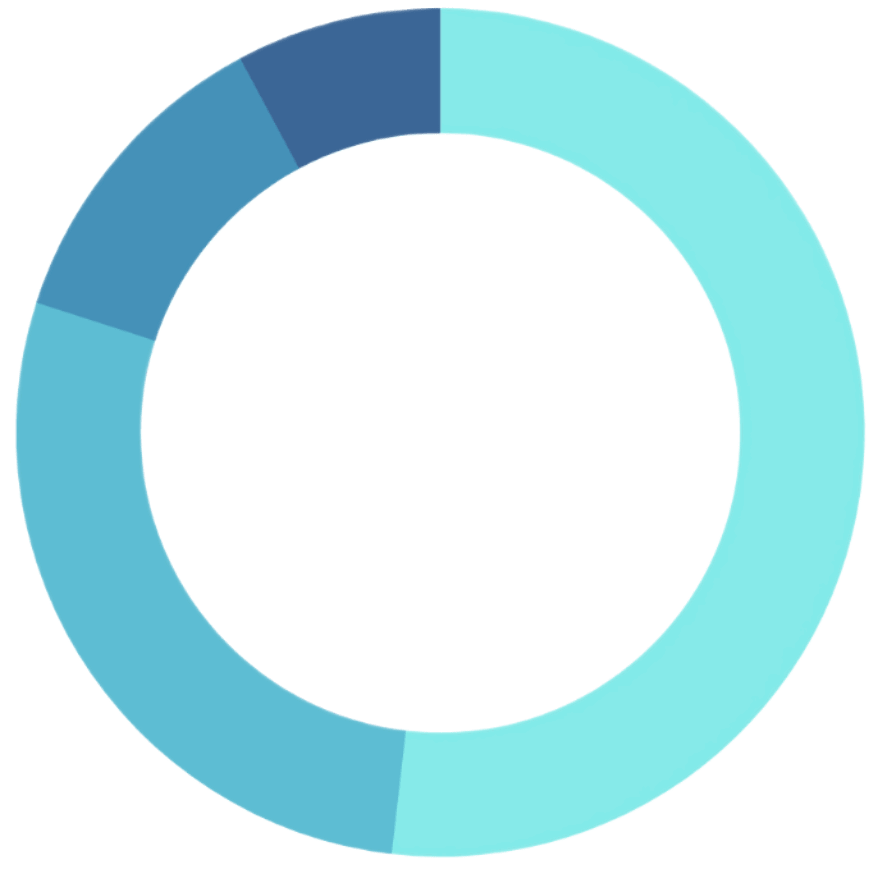
Where Malware Hides
The most common paths used on business PCs in 2022 were:
%temp% — 41.1%
%appdata% — 22.3%
%cache% — 9.7%
%desktop% — 6,2%
— 2023 OpenText Cybersecurity Threat Report
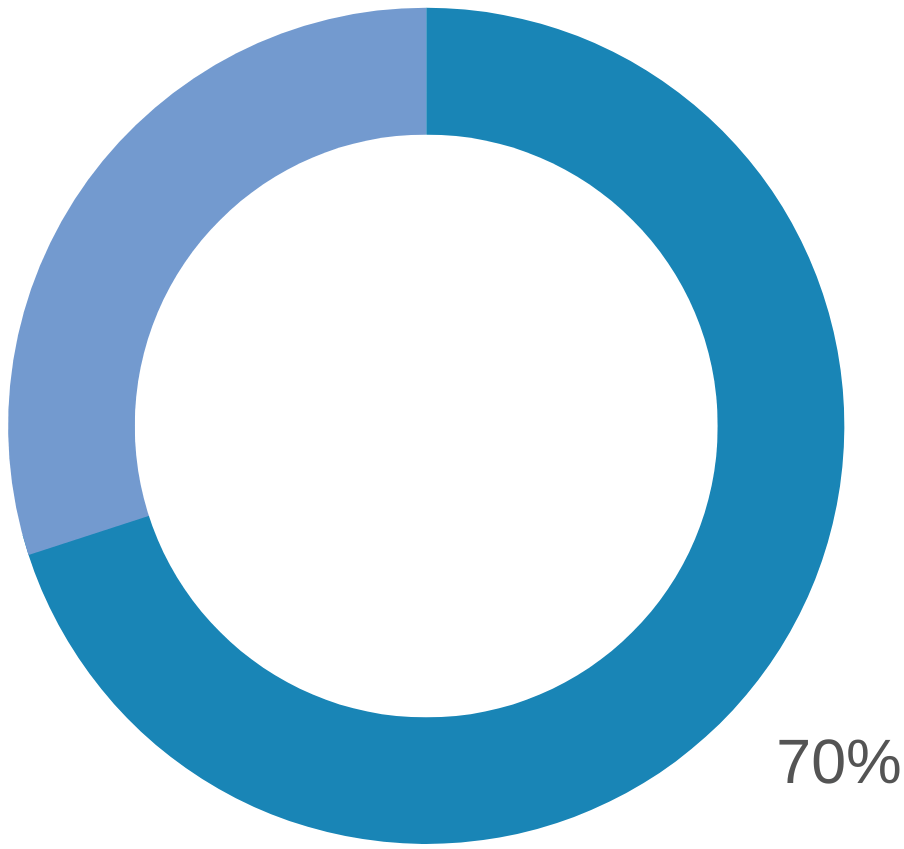
Hidden URLs
The percentage of malicious URLs hidden behind a proxy or a geolocation-masking service is 70% in 2022, a 36% increase compared to 2021. Masking a malicious URL’s location is now easier than ever.
— 2023 OpenText Cybersecurity Threat Report
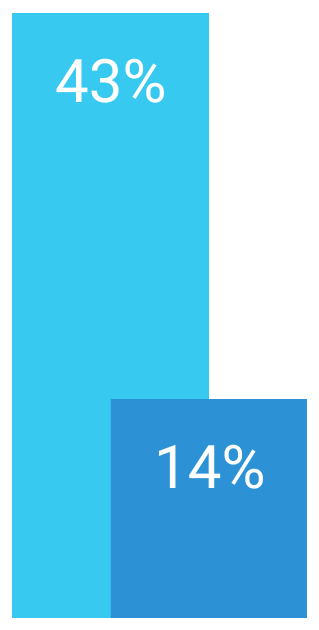
Prevalent Targets: Small Businesses
43% of cyberattacks target small businesses, but just 14% are prepared to defend themselves.
— Accenture 2023 Cost of Cybercrime Study
50K most active malicious IP addresses
Spam Sources
Hosting Phishing Sites
Windows Exploits
Hosting Scanners
Operating Proxies
Other
— BrightCloud 2023 Report