Take This Checklist to Avoid Hollywood Hacking Scenario!
Leaking private photos of Hollywood’s top celebrities strikes the warning alarm of cloud security again. While arguing and discussions around cloud vulnerabilities never cool down, this time the Hollywood sensation is more a lesson about how to use cloud adequately rather than a “to use, or not to” debate, especially for business users.
Why? Simple, we are living in the cloud epoch and the world is just not heading back! So, what can we learn from the disaster this time?
First of all, use cloud attentively and carefully! Keep it in mind that you are on cloud, right now and almost for every second! No matter what you do, what devices you use and what’s the size of your business, hardly you do not use cloud – as a matter of fact, you may be part of the cloud already!
Well then, simple NO.1, DO NOT use simple, easy-to-hack-down passcode – something like a birthday, street number or phone number, or even combinations of them. Sounds easy and common sense? – Yet 70% business cloud users are not following this NO. 1, simple password policy!
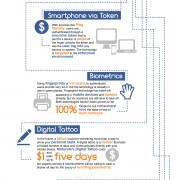
Second, always consider additional security methods to further safeguard your data! Secondary encryption and two-factor authentication are among the top options.
“Secondary encryption” enables the account’s owner to take matters in his/her own hand to protect the data. Rather than relying on built-in encryption or SSL transfers that cloud providers have within their infrastructure, you can leverage other encryption programs such Box Cryptor or TrueCrypt. These programs essentially encrypt your files on the fly prior to storing it on the cloud so that your files remain unreadable even if a hacker manages to steal your password or breach your cloud provider’s normal defense mechanisms.
“Two-factor authentication” may sound jargony and unfamiliar, but it’s actually something you use all the time nowadays. Remember those requests asking for a four or six digits verification code in addition to your username and password, which are usually sent to you via text message? Those random generated, time sensitive codes are “two-factor authentication”. For business users, it can be a lot more varied and strengthened and it can be both virtual and physical, which enforces another powerful defense line for your data security.
Well, as short as this checklist is, it may save you from big trouble and loss! And if you want to learn more, check our IT Security blogs and fuel you up with more professional data-protection tips!
And share this Infographics with you IT management team: